1. Privacy in the Digital Age: The DePIN Movement
Today’s digital communication landscape is filled with potential privacy pitfalls. Every click and message can be tracked by tech giants, governments, or even hackers.
As our digital and physical lives merge, the need for privacy has never been more urgent—or more endangered. Recent incidents, like the Telegram CEO’s clash with French authorities, show that even supposedly secure platforms aren’t safe from scrutiny. With data breaches on the rise and invasive ads tracking our every move, the internet is far from the open, free space it was meant to be.

DePIN projects are stepping up as the digital world’s new guardians of privacy. They leverage blockchain and decentralized technologies to ensure that data isn’t centralized, making it harder for any single entity to control or access user information.
1.1. Session: Reinventing Secure Messaging
Session is a groundbreaking project transforming the landscape of secure communication. Unlike conventional messaging apps, which often compromise privacy by tracking user identities and interactions, Session provides a robust alternative akin to a fortress compared to a cardboard box.
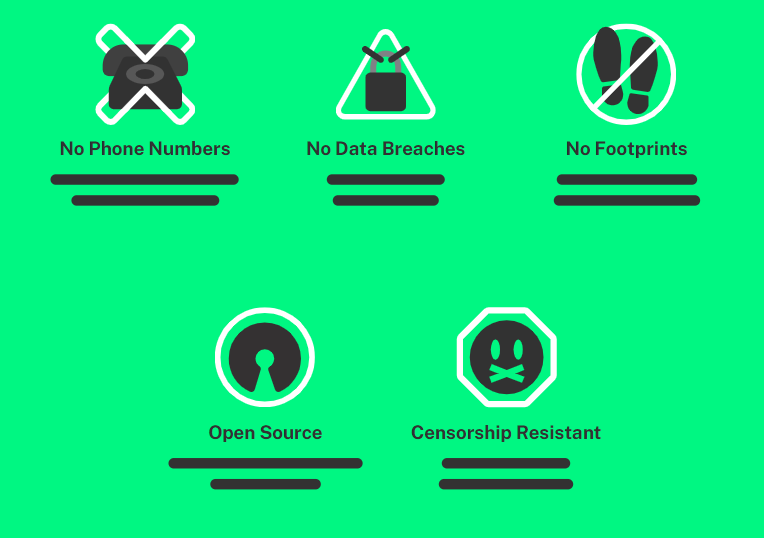
- Privacy Beyond Encryption: While many messaging platforms encrypt messages, they often retain metadata, such as user identities and communication timestamps. Session addresses this privacy gap by eliminating the need for phone numbers or email addresses. Instead, users receive a unique public key, serving as a confidential identifier.
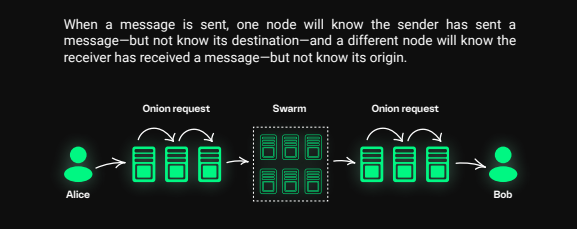
- Decentralized Network Architecture: Session employs a decentralized network of nodes to route messages, ensuring enhanced security. This innovative approach resembles a sophisticated game of telephone, where each node only knows the preceding and succeeding node, maintaining message confidentiality.
- Open-Source Transparency: Being open-source, Session allows public scrutiny of its codebase, ensuring transparency and trust. Users can verify the platform’s security features, ensuring no hidden vulnerabilities are present.
- The Session Protocol Advantage: The Session’s distinct protocol sets it apart. Unlike other encrypted messaging systems that require continuous device synchronization—a potential vulnerability—the Session Protocol operates efficiently in decentralized networks, handling message delays and out-of-order delivery with ease. This adaptability is akin to a postal system that remains functional despite changing routes.
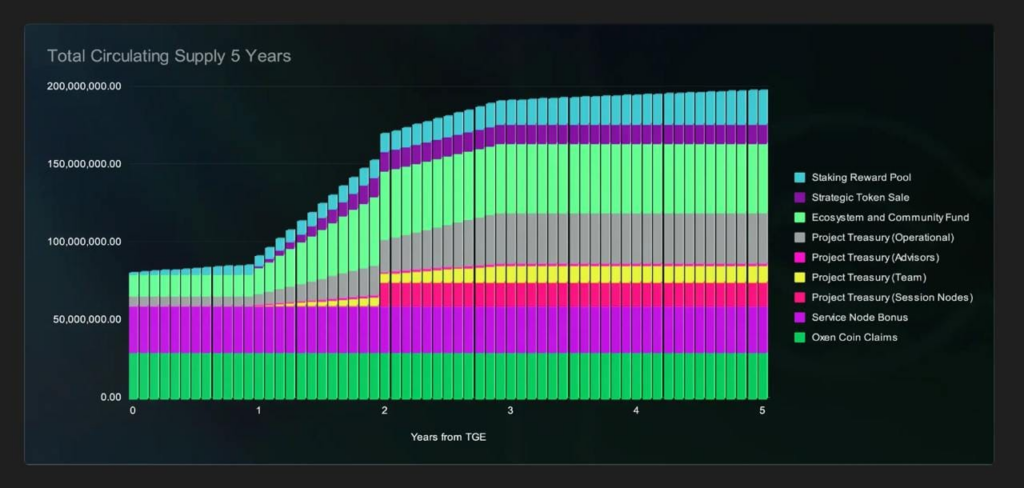
- Tokenomics and Network Functionality: Session introduces the Session Token, slated for launch in 2024 on Arbitrum One, with a capped supply of 240,000,000 tokens and 80,000,000 released at the TGE. These tokens are integral to the network, enabling users to access Session Pro, register unique nicknames through the Session Name Service, and stake tokens to operate Session Nodes. Notably, 90% of tokens spent on services are secured in the Staking Reward Pool, effectively reducing the circulating supply. Further details can be found on our DePIN Hub page.
- Sustainable and Secure Operations: Session’s unique DePIN model ensures the platform is not driven by data monetization. Instead, it relies on a network of incentivized operators committed to maintaining a secure and efficient environment.
The session is poised for growth, focusing on enhancing group chat functionality, improving the user interface, and expanding its node network. However, maintaining speed and reliability while scaling a decentralized network remains a significant challenge. The competitive messaging app market also necessitates continuous innovation.
1.2. Anyone Protocol: A Decentralized VPN for the People
A VPN functions as a secure conduit for internet traffic, concealing users’ locations and safeguarding online activities from prying eyes. Typically, VPN services are managed by companies, which requires users to shift their trust from internet providers to these VPN operators, a compromise that may not always be ideal.
Anyone introduces a novel concept: rather than relying on a single entity, it leverages a decentralized network of relays managed by individuals. This model disperses internet traffic across various relays, enhancing privacy and security. The network’s decentralized nature resembles a global relay race for data, increasing resilience and reducing vulnerabilities.

- Incentive Structure and Governance: Central to Anyone’s innovation is its incentive mechanism. Relay operators earn $ANYONE tokens for providing bandwidth, promoting a robust and efficient network. These tokens are integral to the network’s governance and security, as holders stake to operate relays and bolster network integrity. Additionally, tokens facilitate premium service payments, expanding the ecosystem.
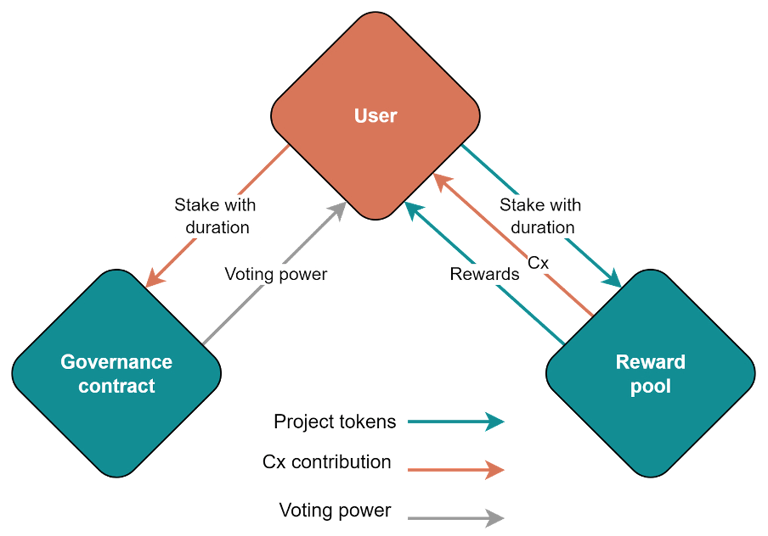
- Decentralized Resilience: Beyond privacy, Anyone aims to create a more resilient internet infrastructure. By distributing control across numerous relays and employing decentralized management, the network minimizes the risk of single points of failure, ensuring stability and reliability.
- Anyone Router: Simplifying Participation: The Anyone Router, a user-friendly hardware solution, allows individuals to join the network effortlessly and earn tokens. This device democratizes access to decentralized privacy, making it accessible to a broader audience.
Anyone is poised to integrate its technology into diverse applications, potentially revolutionizing online privacy. The vision includes seamless data routing through secure, decentralized networks across all applications. However, challenges persist, including regulatory concerns, potential misuse, and maintaining token economics. With a committed community and strategic vision, Anyone is well-positioned to advance decentralized privacy.
1.3. Acurast: Redefining the Cloud with Decentralization
Acurast is transforming the digital landscape by reimagining cloud computing. Unlike traditional models that rely on large data centers, Acurast envisions a world where millions of devices globally contribute to a decentralized, serverless cloud network.
Acurast proposes a groundbreaking solution: utilizing everyday devices, like old smartphones, as part of a global network. This allows individuals to provide computing power and earn rewards, enhancing security and privacy while reducing dependence on major tech companies.

- Incentivizing Participation: Participants in the Acurast network are rewarded through transaction fees and protocol incentives. This model encourages widespread involvement and supports the network’s growth and sustainability.
- Expansive Applications: The applications for Acurast’s technology are extensive. It enables secure machine learning on sensitive data and financial transaction processing with robust security, all without relying on centralized institutions.

2. Challenges and the Path Forward
DePIN projects face hurdles such as scalability, usability, and regulatory pressures. Scaling decentralized networks to serve millions while maintaining speed and security is complex. Usability is crucial to attracting mainstream adoption, requiring these technologies to be as user-friendly as current centralized solutions.
Despite these challenges, DePIN projects are building a foundation for the Internet where privacy is a fundamental right. They empower users to take control of their data and communication, transforming the digital landscape.
The information provided in this article is for reference only and should not be taken as investment advice. All investment decisions should be based on thorough research and personal evaluation.





