The hype around cryptocurrencies can largely be attributed to price speculation by retail investors seeking profits. However, for blockchain technology to gain widespread adoption, it must demonstrate use cases beyond speculative trading. The emergence of blockchain-based decentralized identity (DID) solutions could provide the next major use case to attract millions of new users.
I. Problems with current ID solutions in general
In essence, identity represents the mechanisms by which individuals can be recognized, affirmed as the owner of certain possessions, and acknowledged for their actions. Such identity credentials include driver’s licenses, national identification cards, passports, social media accounts, and professional certifications… However, these traditional forms of identity commonly suffer from one or both of the following shortcomings.
1. Forgery
For instance, an individual can fabricate a medical examination document with a counterfeit hospital seal.
Besides, we often think of the issue of age verification on dating apps, as individuals can easily deceive others about their age. The fact that they have joined the app indicates their desire to participate, even if it means falsifying their age.
2. Transfer
One can lease their pharmacist license to a party seeking to establish a pharmacy.
An individual unlawfully transfers their voting rights to another person in exchange for personal gain. The recipient fraudulently exercises the transferred voting right, undermining the integrity of the electoral process.
Another example that highlights the shortcomings of existing identity systems in a more entertainment-focused context is as follows: Let’s say I want to provide evidence that I have been a devoted follower and supporter of my favorite celebrity since before they gained widespread fame. I claim that my Facebook account has been consistently posting pictures of them since 2013. How reliable would my assertion be in terms of accuracy?
Likewise, we observe that current identity systems inadequately address issues such as forgery and the renting of licenses, thereby allowing these activities to persist.
II. Problems with Centralized ID solutions in particular
1. Personal data breach
Centralized identity systems, however, present an additional concern whereby individuals are compelled to divulge unnecessary personal information. For instance, in the context of banking, the only pertinent details for the institution would be whether one is of legal age and possesses a valid national identification card. The disclosure of additional information, such as one’s date of birth, could result in the reception of annoying targeted advertisements on birthdays.
Both the issuing authority and the entity responsible for verifying one’s identity retain control over the input and output of such information. By control, it implies that the system retains this data on behalf of the individual (such as LinkedIn retaining digital certifications or Facebook storing your content), while simultaneously determining which specific details can be shared.
The issue of data breaches, although it may not have fully engendered real awareness among many individuals, raises the question of what actionable measures can be taken. This predicament originates from inherent flaws within the systems themselves, making it arduous for individuals to rectify.
2. Inconvenient user experience
Centralized identity platforms can limit interoperability due to their reliance on proprietary systems and closed architectures. These platforms often require strict adherence to a specific centralized authority or organization, making it challenging to integrate with external systems that operate on different protocols.
The practice of repeatedly uploading documents like passports, driver’s licenses, and health certificates can be cumbersome and time-consuming for individuals. It often involves providing the same information and documents to different entities or platforms for various verification purposes. This repetitive process can lead to inefficiencies, potential errors, and unnecessary duplication of personal data.
III. What is Decentralized ID?
Decentralized ID refers to a concept and technology that allows individuals to have control over their own digital identity without relying on centralized authorities or institutions. It is also sometimes referred to as self-sovereign identity (SSI).
DID consists of two main components: decentralized identifiers (DIDs) and verifiable credentials (VCs). DIDs are similar to traditional identifiers such as names or email addresses but are controlled and issued by individuals themselves. They are stored on encrypted decentralized digital ledgers, typically blockchains, rather than in a central repository. VCs, on the other hand, are credentials derived from familiar documents like diplomas, passports, or library cards. These credentials are also stored on a blockchain and can be read by machines, providing cryptographic verifiability and accessibility.
DID has the potential to mitigate fraud, data breaches, social engineering, and theft in various sectors, including education, healthcare, law, travel, and employment. It can revolutionize identity management by allowing individuals to have more control over their personal information and enabling secure and trusted interactions online.
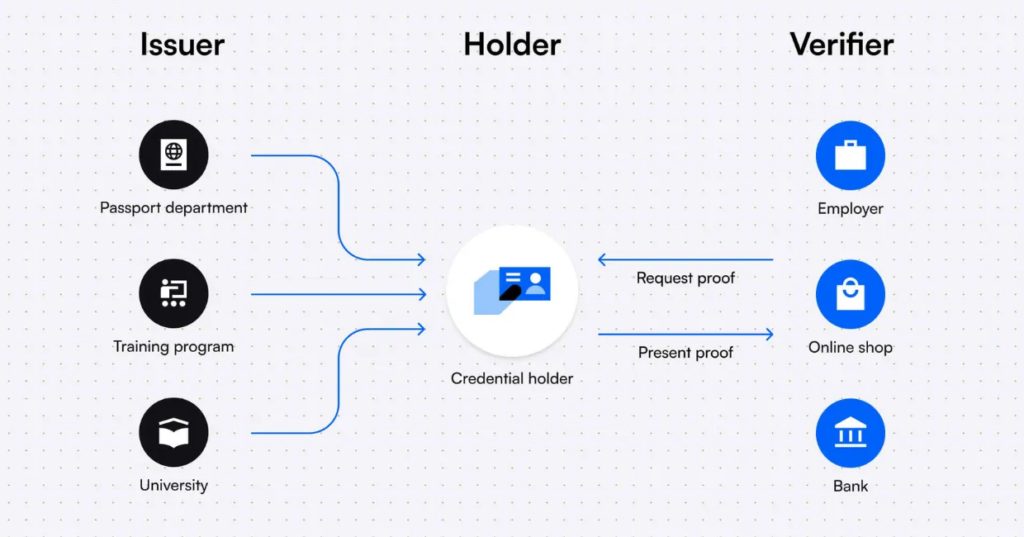
IV. Forms of Dencentralized ID
1. Soulbound token
1.1. Definition
A Soulbound token represents a distinct class of tokens that possess unique ownership and transfer characteristics. These tokens are exclusively owned and capable of being transferred by a specific address. Once a Soulbound token is generated and assigned to an address, it becomes permanently linked to that address, rendering any transfer or ownership by other addresses impossible. This attribute ensures a heightened level of security and control for both the token owner and any individuals temporarily holding the token.
The utilization of Soulbound tokens can be justified by several compelling factors:
- Security: Soulbound tokens offer heightened security measures for digital assets, as they are exclusively owned and transferable by a designated address. This impedes unauthorized individuals from gaining access to or transferring these assets.
- Control: Owning a Soulbound token bestows complete control over the associated assets, guaranteeing that they can only be transferred or owned by the address specified in the token.
- Customization: Soulbound tokens can be personalized and adjusted to suit individual requirements, enabling the creation of distinctive digital assets that accurately reflect personal values and interests.
1.2. POAP Protocol
POAP, also known as the “proof of attendance protocol,” exemplifies a project striving to achieve a specific objective. POAP serves as a standard that enables the issuance of NFTs representing an individual’s personal participation in an event.
POAP stands out as an ideal case for implementing the concept of soulbound tokens. When someone views your POAP, their interest lies not in whether you paid someone who attended the event but in whether you personally were present at the event. Similar challenges arise when contemplating the on-chain inclusion of certificates such as driver’s licenses, university degrees, or proof of age. The value of these certificates diminishes significantly if individuals who don’t meet the specified conditions can simply purchase them from others who do.
While transferable NFTs have their own significance and can greatly support artists and charitable causes, there remains a vast and unexplored design space for non-transferable NFTs and the possibilities they hold.
2. Proof of Personhood
2.1. Definition
According to Worldcoin Foundation, in a nutshell, proof of personhood (PoP) is a mechanism that digitally verifies an individual’s humanness and uniqueness. It can be thought of as the first and most fundamental building block in establishing digital identity.
"It creates a list of public keys where the system guarantees that each key is controlled by a unique human. In other words, if you're a human, you can put one key on the list, but you can't put two keys on the list, and if you're a bot you can't put any keys on the list." - Vitalik
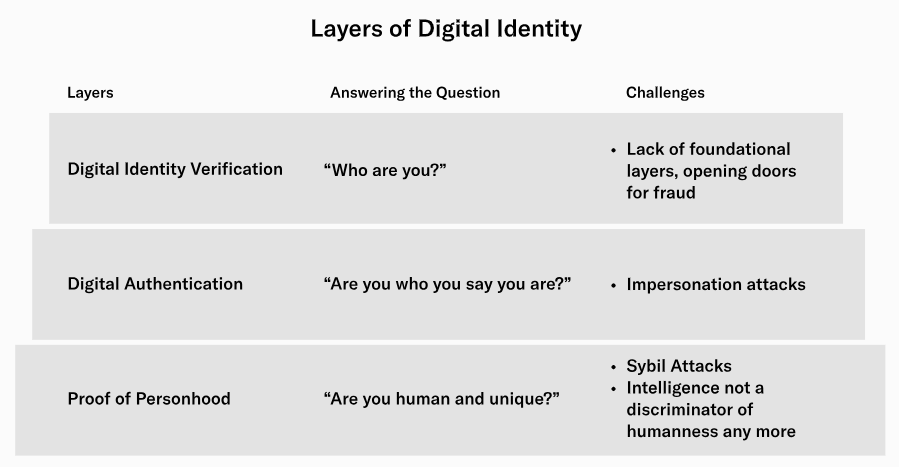
Proof of personhood holds significant value as it effectively resolves various challenges related to anti-spam measures and the prevention of power concentration. It does so without relying on centralized authorities and by disclosing the least amount of information necessary. The absence of a solution for proof of personhood would make decentralized governance, including “micro-governance” such as social media post voting, highly susceptible to capture by wealthy entities, including hostile governments.
In the absence of proof of personhood, many services would be compelled to combat denial-of-service attacks by imposing access fees. However, the price required to deter attackers may also prove prohibitively high for many legitimate users with lower incomes.
Presently, numerous prominent applications address this issue by utilizing identity systems backed by governments, such as credit cards and passports. While this approach resolves the problem, it often entails significant sacrifices in terms of privacy, and governments themselves can easily exploit these systems through attacks.
2.2. Worldcoin
Worldcoin proposes a biometric-based solution using specialized hardware called “the Orb” to scan users’ irises and ensure each registered account is controlled by a unique human. The project plans to distribute Orbs globally, prioritize user privacy with cryptographic techniques, and eventually decentralize its governance.
There are plenty of Worldcoin use cases:
- Airdrops for token distributions
- Token or NFT sales that give more favorable terms to less-wealthy users
- Voting in DAOs
- A way to “seed” graph-based reputation systems
- Quadratic voting (and funding, and attention payments)
- Protection against bots / sybil attacks on social media
- An alternative to captchas for preventing DoS attacks
While Worldcoin’s approach has gained attention, it has also faced criticism. Concerns include privacy and security risks associated with the Orb, design flaws in its digital currency, and potential ethical implications. Critics question the overall concept of biometric proof of personhood, highlighting risks such as privacy breaches, loss of internet anonymity, and vulnerability to coercion by authoritarian regimes.
V. Challenges of Decentralized ID solutions
The core principles of decentralized identity and the current state of the decentralized identity ecosystem demonstrate the positive benefits it brings to identity management. However, it is crucial to explore the challenges and solutions related to decentralized identity in order to foster its growth. Below are some notable obstacles that can be encountered in the field of decentralized identity.
| Challenges | Description | Current Solution |
| Privacy and Security | Ensuring strong security and user privacy; users control their data and manage disclosure. | Implementing zk-SNARK technology, robust encryption, and secure key management. |
| Interoperability | Seamless use of DIDs across platforms without multiple registrations. Common standards needed. | W3C’s Decentralized Identifiers (DIDs) v1.0 provides common standards for DID solutions. |
| User Adoption and Usability | Encouraging adoption and making DIDs user-friendly and intuitive. | Cardano and other blockchain networks are developing non-custodial digital identity wallets. |
| Governance and Regulation | Establishing governance and complying with legal frameworks while maintaining decentralization. | Governments (e.g., US, Canada EU) exploring DIDs; Istanbul using Omchain’s proof-of-identity (PoI) for privacy. |
1. Privacy and Security
Protecting user privacy and maintaining strong security measures are paramount in decentralized ID solutions. Users should have control over their personal data and be able to manage its disclosure. Implementing robust encryption, secure key management, and privacy-enhancing technologies becomes crucial to prevent unauthorized access and data breaches.
"Such selective reveals are certainly possible with zk-SNARK technology, but we are yet to see a large-scale deployment of such solutions."Adam Gągol, co-founder of Aleph Zero
2. Interoperability
Achieving interoperability between different DID systems is essential for seamless user experiences and widespread adoption. Users should be able to use their DIDs across various platforms and services without the need for multiple registrations or identity verifications. Developing common standards and protocols is necessary to enable interoperability among DID solutions.
However, recent agreement on DI standards is accelerating progress. W3C established Decentralized Identifiers (DIDs) v1.0 which describes the technological details and standards that organizations creating DID solutions can follow. W3C describes DID as being “A new type of identifier that enables verifiable, decentralized digital identity.”
"A high level of interoperability becomes possible once every provider uses the same specification." - Rouven Heck, decentralized identity lead at ConsenSys Mesh and executive director at the Decentralized Identity Foundation
3. User Adoption and Usability
Encouraging user adoption of DID solutions can be challenging, especially when they involve new technologies or complex user interfaces. The solution should be user-friendly, intuitive, and provide clear benefits to traditional centralized identity systems. Educating users about the advantages of DIDs and addressing usability concerns are crucial for widespread acceptance.
Cardano, along with several other blockchain networks, is actively working on the development of its own non-custodial digital identity wallet.

4. Governance and Regulation
Establishing governance mechanisms and addressing regulatory requirements are important for DID solutions. Clear guidelines and frameworks need to be developed to ensure compliance with legal and regulatory frameworks while maintaining the decentralized nature of the system. Balancing innovation, user empowerment, and regulatory compliance is a significant challenge in this space.
Today, some governments, including the United States, Canada, the European Union, Germany and Finland, have been looking at DID “as a tool to improve state-backed identity solutions”.
Istanbul is employing decentralized identity solutions to enhance data privacy, using Omchain’s proof-of-identity (PoI), which operates without the need for database queries during authentication.
The information provided in this article is for reference only and should not be taken as investment advice. All investment decisions should be based on thorough research and personal evaluation.






[…] Decentralized ID – non-speculative use case to attract the next billions users […]
Comments are closed.